|
'분류 전체보기'에 해당되는 글 167건
[Schizo!, 2008. 12. 7. 13:56, 취미생활/game]
'취미생활 > game' 카테고리의 다른 글
[Schizo!, 2008. 12. 7. 00:11, 취미생활/game]
★그래픽 옵션 제한 풀기
1. 게임이 설치된 폴더에 commandline.txt 파일을 생성. 2. commandline.txt 내용에 -norestrictions라고 입력. 3. 게임을 실행하여 옵션을 조절. ★창모드 commandline.txt 내용에 -windowed ★fsaa 사용(이 옵션의 실효성에 대해서는 아직 말이 많음) // 안되는듯합니다. commandline.txt 내용에 /fsaa 입력 ★종합 셋 다 하려면 commandline.txt에 -norestrictions -windowed /fsaa 입력 '취미생활 > game' 카테고리의 다른 글
[Schizo!, 2008. 12. 6. 09:27, 취미생활/game]
 초반 It's Your Call 미션 후 십자키의 윗부분을 두번 터치하여 번호를 입력하고 샌드부분 터치하시면 실행. 359-555-0100 : 경찰헬기 소환 227-555-0100 : FIB (FBI가 타는 검고 큰 지프차) 자동차 소환 227-555-0142 : Cognoscenti (차체가 긴 고급차) 자동차 소환 227-555-0175 : Comet 자동차 소환 227-555-0168 : Spuer GT (경주용 스포츠카) 자동차 소환 227-555-0147 : Turismo (스포츠카) 자동차 소환 625-555-0150 : Sanchez (산악용오토바이) 바이크 소환 625-555-0100 : NRG-900 바이크 소환 938-555-0100 : Jet MAX 보트 소환 326-555-0100 : 방탄복 100%충전 482-555-0100 : 체력 100%충전 486-555-0150 : 무기세트1 야구배트,권총,샷건(산탄총),MP-10(머신건),M4(머신건),스나이퍼총,RPG(로켓런쳐),수류탄 486-555-0100 : 무기세트2 칼,화염병,권총,샷건(산탄총),Uzi(머신건),AK47,스나이퍼총,RPG(로켓런쳐) 486-555-0100 : 날씨바꾸기 267-555-0150 : 지명수배 레벨 올리기 267-555-0100 : 지명수배 레벨 내리기 Song information(치트 적용시 핸드폰으로 노래정보와 아티스트 정보를 문자로보내줌) GTA4안에서 나오는 노래 정보. 948-555-0100. '취미생활 > game' 카테고리의 다른 글
[Schizo!, 2008. 11. 28. 20:01, 정보]
어느덧 벌써 연말이군요.
대인배 오프라 윈프리 누님께서 크리스마스 캐럴 8곡을 쏩니다. 아마 내일까지 무료로 알고 있습니다. http://www.oprah.com/article/oprahshow/20081118_tows_holiday/2 '정보' 카테고리의 다른 글
[Schizo!, 2008. 11. 28. 09:27, 정보]
http://www.tivir.com/ 회원 가입후 TV수신료 납부 영수증을 스캔이나 디카로 찍어서 제출. 다른 자동녹화서비스에 비해 화질이 좋고, (720p까지 선택가능) 다른 곳은 유료인데 반해 무료라는게 장점
'정보' 카테고리의 다른 글
[Schizo!, 2008. 11. 27. 02:23, 정보]
우연히 봤는데(테스트폰인듯) 찾아보니 크레이브 zn40 이라고 합니다. dmb가 되는 듯 하고, 이뻤음! 저 투명한 커버에 달린 모토로라 엠블럼에서 소리가 나오는지 궁금함 '정보' 카테고리의 다른 글
[Schizo!, 2008. 11. 22. 22:38, study/ccna]
ccna 2 final Why would an administrator change the value highlighted in the exhibit? (Choose two.) -to make the router bypass the startup-configuration file -to configure the router to boot the RXBOOT image During initial router bootup the following line appears: -The router has not been configured. -The startup-config file cannot be located. A new technician must add boot system commands to one of the department routers. Which available commands will the router return as output when the command shown below is entered? (Choose two.) -TFTP -FLASH What information can be learned during the initial router bootup? (Choose two.) -the number and types of interfaces installed -the router model and the amount of memory that is available Which of the following are primary functions of a router? (Choose two.) -packet switching -Path selection
-Montgomery has Layer 2 connectivity with Cumberland. -Brant, Fisherman, and Potomac are directly connected to Montgomery. Which router components and operations are correctly described? (Choose two.) NVRAM - stores the configuration file POST - runs diagnostics on hardware modules What are the results of setting the boot field bits in the configuration register to "0000"? (Choose two.) -The router will enter ROM monitor mode upon reload. Which commands will correctly configure an extended ACL? (Choose two.) -Router(config)# access-list 192 permit icmp host 198.18.4.3 172.22.0.255 0.0.0.0 echo -Router(config)# access-list 153 deny udp 10.43.0.0 0.0.255.255 any eq 161 Which commands will show the status and IP address of all interfaces on a router? (Choose two.) -show protocols -show interfaces An administrator needs to determine if RIP v1 or IGRP should be used in a small network. Which two statements are true and should be considered by the administrator before making the decision? (Choose two.) -IGRP will use the available bandwidth and calculated traffic delays on the link to help determine the best path. -IGRP can be implemented on large networks up to 255 hops in diameter. Which of the following statements are true regarding routed protocols? (Choose two.) -They provide enough information in the Layer 3 address to allow a packet to be forwarded from one network to another. -They carry user data between networks. Which two steps describe how to create a functional physical connection between a router console and a terminal? (Choose two.) -Use an RJ-45 to DB-9 adapter on the terminal serial port to connect to the cable going to the router console. -Use a rollover cable to connect from a terminal serial port to the router console port. What are two possible reasons a router would not load a valid IOS from flash? (Choose two.) -The first boot system command executed in the startup configuration file is boot system rom. -The configuration register is set to 0x2100. access-list 199 deny tcp 198.18.0.0 0.0.255.255 any eq 25 -SMTP traffic from hosts on network 198.18.0.0 will be denied. -SMTP and HTTP traffic to hosts on the 198.18.0.0 network is permitted.
-This is a named extended ACL that allows any host on 192.168.85.0 to Telnet to address 172.25.0.26. -All FTP and HTTP traffic destined for 172.25.0.26 will be denied.
-ATL# 192.168.4.2 -CHI# telnet 192.168.4.1 From the running-config, the following configuration entries are displayed: -Three Telnet lines are available for remote access. -Remote access to this local router will require a Telnet password of g8k33pr. What are two characteristics of the support for Telnet within Cisco IOS software? (Choose two.) -Up to five separate Telnet lines are supported by default in standard edition IOS files. -A router can host simultaneous Telnet sessions. What are two recommended uses of login banners? (Choose two.) -to display security warning messages -to announce a scheduled system shutdown Which features describe a FastEthernet interface on a router? (Choose two.) -may be administratively disabled by using the shutdown command -must be configured with a valid IP address and subnet mask in order to forward packets What will occur if the command service password-encryption is entered on a router? (Choose two). -It will apply a weak encryption to all unencrypted passwords. -It will configure the user EXEC mode, telnet, and enable passwords as encrypted. Choose 3 Which procedures will work while configuring the router using the setup configuration utility? (Choose three.) -Press Enter or the Return key to accept the default values. -Enter the address on an interface or add a new routing protocol suite. -Press Ctrl-C to return to the privileged mode prompt or to terminate setup mode.
-modem -DCE device -CSU/DSU
-Marketing(config)# ip route 0.0.0.0 0.0.0.0 fa0/0 -Sales(config)# ip route 192.0.2.0 255.255.255.0 fa0/0 -Sales(config)# ip route 0.0.0.0 0.0.0.0 s0/0
-The version for this IOS file is 12.1 release 5. -Where the file is stored on the router and whether the file is relocatable is indicated by the expression mz. -This image could be used on a 2621 or a 2620 with enough RAM. What are three features of CDP? (Choose three.) -provides information on directly connected devices that have CDP enabled -tests Layer 2 connectivity -enabled by default on each interface The following access list has been correctly applied to a router interface: -A wildcard mask of 0.0.0.0 is assumed for 172.30.65.52. -All traffic from 172.30.65.51 will be permitted. -This is a standard IP access list. Why are interface descriptions used in router configurations? (Choose three). -to enable support personnel to easily identify networks and customers that may be affected by a possible interface issue -to provide comments on the interface without affecting the router functionality -to identify the purpose and location of the interface Single answer In what order will the initial startup routine of a router locate and load the IOS if the config-register setting is 0x2102 and there are no boot system commands present in the startup-config file? -Flash, TFTP server, ROM
-Networks 198.18.100.0/24 and 172.23.0.0/16 will be unreachable from Marshall and Fiji.
-The ip classless command is not enabled on Router A.
-B(config)# router rip Which router component stores the information that is displayed by the show arp command? -RAM If a PC does not have network connectivity to a router, which router port can be used to establish communication? -Console What can a network administrator do to recover from a lost router password? -boot the router to ROM monitor mode and configure the router to ignore NVRAM when it initializes
-Tokyo(config)# interface fa0/0 A network administrator must configure a FastEthernet interface with an IP address. The configuration must also identify the remote site to which the interface is connected. Which set of commands will meet these requirements? -StPetersburg(config)# interface fa0/0 A network administrator issues the erase startup-config command on a configured router with the configuration register set to 0x2102 and observes the following output: -The router will prompt the user to enter setup mode or to continue without entering setup mode. The main router of XYZ company has enough flash and RAM to store multiple IOS images. An administrator wants to upload a second IOS image from a TFTP server to the flash of the router. Which method will accomplish this task? -Copy the IOS image file from a TFTP server using the command copy tftp flash. When prompted, provide the IP address or name of the TFTP server and the IOS image filename.
-ROM
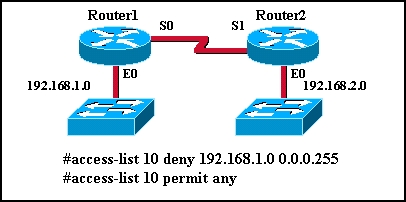
-access-list 33 deny 172.16.34.0 0.0.0.255
-5 seconds
-WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1
-access-list 125 permit ip 192.168.2.0 0.0.0.255 any
-The Finance Admin host and the HR Admin host will be able to ping to each other. The HR Admin host will be allowed to access Web servers on the Internet, while the Finance Admin host will be denied Internet Web access.
-Use the show interfaces command from a Telnet session on router B to check the connection to router C.
-A, B, D, E, F What can be determined from this output? -57625 is a composite metric used by IGRP in calculating the best path. 'study > ccna' 카테고리의 다른 글
[Schizo!, 2008. 11. 19. 00:52, 취미생활/아이팟터치]
한곳은 애플에 의해 폐쇄되었고..나머지 한곳 마져 접속이 안되네요... '취미생활 > 아이팟터치' 카테고리의 다른 글
[Schizo!, 2008. 11. 14. 01:38, 자료]
'자료' 카테고리의 다른 글
[Schizo!, 2008. 11. 12. 00:50, 정보]
학교 컴퓨터 - usb를 통해서 바이러스가 감염된것 같다.
범인은 오토런 바이러스의 변종인 se520.exe 바이러스 고생하다가 한동안 지웠었던 카스퍼스키 안티 7.0 깔고 바로 해결. 바이러스에 대해 검색하다가 좋은사이트 하나 발견! http://www.virscan.org/ '정보' 카테고리의 다른 글
[Schizo!, 2008. 11. 11. 22:14, 정보]
베이스가 좀 강하게 울림...커널형이라 그런지 '정보' 카테고리의 다른 글
[Schizo!, 2008. 11. 8. 12:57, study/ccna]
1 Which statements are true regarding the significance of the access control list wildcard mask 0.0.0.7? (Choose two.) 8 • Router1# configure terminal Router(config)# access-list 2 deny 172.16.5.24 What can be concluded about this set of commands? 15 Which statement is true regarding wildcard masks? 17 Which of the following matches an ACL identification number with the correct protocol?(Choose three.) 'study > ccna' 카테고리의 다른 글
[Schizo!, 2008. 10. 31. 16:43, 취미생활/game]
=================================
레드 얼럿 3 한글 개선 패치 알파 1.03V ================================= 적용방법 : 레드얼럿3가 인스톨된 폴더의 data 폴더에 복사. 원본은 백업을 권장할 가치도 못 느끼므로 그냥 덮어쓰기할 것. [버그 수정] *한글 개선 패치 후 메인 화면 입장이 느려지던 버그를 수정 ================================= 레드 얼럿 3 한글 개선 패치 알파 1.02V ================================= 적용방법 : 레드얼럿3가 인스톨된 폴더의 data 폴더에 복사. 원본은 백업을 권장할 가치도 못 느끼므로 그냥 덮어쓰기할 것. [동영상 자막 싱크 수정] *오프닝 *소련 미션 1 *소련 미션 2 *소련 미션 3 *소련 미션 4 [오타 수정] *20개 정도 단어의 오타 추가 수정 [맞춤법 수정] *30여개 문장의 틀린 맞춤법 추가 개선 [단어 수정] *항구 - 조선소 *기갑차량 기지 - 기갑 제조소 *평화군 - 평화유지군 [미션 제목 수정] *얼어붙은 항구를 탈환하라 - 얼어붙은 항구 탈환 ================================= 레드 얼럿 3 한글 개선 패치 알파 1.01V ================================= [오타 수정] *170개 정도 단어의 오타 수정 [맞춤법 수정] *320여개 문장의 틀린 맞춤법 개선 [단어 수정] *적색분자 - 빨갱이 *사이오닉 파멸기 - 정신력 학살기 *스커미시 - 모의전투 *장면 - 영상 *크렘린, 크레믈린, 크레물린 - 크레믈린으로 통일 *커맨드 앤 컨커 - 레드얼럿 *아레나 - 경기장 *랠리 포인트 - 집결 지점 *점프 - 도약 *크러셔 - 파쇄 *징집군 - 징집병 *국왕 - 황제 *레이다 - 레이더 *장면 - 영상 *소비에트 - 소련 *테슬라 기계보병 - 테슬라 기갑병 *플라즈마커터캐논 - 플라즈마 절단포 *타워 - 탑 *터렛 - 포탑 *소형 잠수함 - 잠수정 *어포칼립스 - 아포칼립스 *수상 - 서기장 *검은 거북 - 현무 *쿠르코브, 크루코브 - 크루코프로 통일 *엑스큐셔너 - 집행자 *축출 - 숙청 *모스코바 - 모스크바 [미션 제목 수정] *달은 그들을 소유하지 않는다 - 달은 그들에게 넘겨주지 않는다 (The Moon Shall Never Have Them) *광기의 유물 - 광기의 기념비 (A Monument to Madness) *시들어에 큰 사과 - 빅 애플을 초토화시켜라 (Blight on the Big Apple) *이스터 섬 - 석상 - 알려진 목격자??? - 돌로 된 얼굴의 목격자 (The Stone-Faced Witnesses) *삶에 길들여진 신 - 살아있는 신을 잡아라 (To Tame a Living God) *내일의 배반자 - 배반자 없는 내일 (No Traitors Tomorrow) *과학의 전쟁 - 전쟁과학 (The Science of War) *2007년 3월의 붉은 군대 - 붉은 군대의 행진 (March of the Red Army) *얼어버린 항구 - 얼어붙은 항구를 탈환하라 (Taking Back the Ice Harbor) *배반의 서커스 - 위험한 서커스 (Circus of Treachery) *욱일의 공습 - 때까치와 가시나무 (The Shrike and the Thorn) 출저 : Red2.net '취미생활 > game' 카테고리의 다른 글
[Schizo!, 2008. 10. 28. 09:15, study/ccna]
1 Which of the following describe how TCP adds reliability to communication? (Choose three.) 2 A computer programmer is developing software that requires a reliable stream of data. Which protocol can be used in the software design to eliminate the need for building error detection and recovery into the application program? 3 Why is TCP considered a connection-oriented protocol? 6 How are originating source port numbers assigned during the data encapsulation process? 7 Which of the following would an administrator do to defend against a denial of service SYN flooding attack? (Choose two.) 8 When a host receives a data segment, what allows the host to determine which application should receive the segment? 11 In the TCP header, which of the following determines the amount of data that can be sent before receiving an acknowledgment? 13 Which of the following protocols uses UDP for transport layer services? 14 What type of segment and data is shown in the graphic? 15 What is the purpose of Positive Acknowledgment and Retransmission (PAR)? 16 Which of the following are functions of the TCP protocol? (Choose three.) 17 What is used by both TCP and UDP when creating a segment? 18 Which authority has control over the assignment of port numbers for applications? 19 Which of the following describe types of port numbers that can be represented in the headers of TCP and UDP segments? (Choose three.) 20 What is the purpose of the three-way handshake that occurs between hosts using TCP as the transport layer protocol? 21 During the encapsulation process, in which order are the IP address, MAC address, and port number assigned when the router is establishing communication with the TFTP server? 23 Which transport layer unit of information places the port number in the header? 'study > ccna' 카테고리의 다른 글
[Schizo!, 2008. 10. 28. 09:11, study/ccna]
1 Tracing the route to Router_D (192.168.4.2) What can be concluded about the network shown in the graphic based on the output given? 2 Which of the following would be the default administrative distance of a static IP route that references the IP address of the next hop? 3 After issuing the show interfaces command, a technician notices the line "Serial1 is down, line protocol is down" in the output. Which of the following are possible reasons for this message output? (Choose three.) 5 9 The network administrator is using a PC to access a router via the router console port. Both the PC and the router are powered on and a cable has been connected between them. However, a session cannot be established. Which steps might fix this problem? (Choose two.) 10 Which command will display routing table information about all known networks and subnetworks? 14 16 Which items would be displayed when the show ip protocols command is executed? (Choose three.) 17 Which two are true regarding the debug commands? (Choose two.) 18 A network administrator suspects that a network is not being included in the routing updates. Which command will provide information on when the next update is due and which networks are advertised in the update? 21 Which of the following are advantages of using a static route? (Choose three.) 'study > ccna' 카테고리의 다른 글
[Schizo!, 2008. 10. 25. 14:50, study/ccna]
1 How does a source host use ICMP to confirm that a destination host is reachable? 2 Which type of message is generated by a host when the ping command is entered? 4 Which two statements are true regarding ICMP? (Choose two.) 5 How does ICMP improve data transfer reliability in IP networks? 6 Which layer protocols provide reliability for IP when needed? 7 Which devices along a data transmission path are notified by ICMP when delivery failures occur? 8 When a datagram is processed by a router on the path from source to destination, what happens to the value in the TTL field?" 9 Which condition could cause a fragmentation needed ICMP destination unreachable message to be sent? 10 11 Which three conditions must be met in order for host to host communication over an internetwork to occur on IP networks? (Choose three.) 'study > ccna' 카테고리의 다른 글
[Schizo!, 2008. 10. 25. 14:49, study/ccna]
1 Which command or set of commands will stop the RIP routing process? 3 Which of the following functions are performed by a router as routing information travels through the network? (Choose two.) 4 What do distance vector algorithms require each router in the network to send? 6 7 Which command will display RIP activity as it occurs on a router? 9 10 How would an administrator configure a static route for use if a primary route failed? 11 Which statements describe RIP? (Choose three.) 12 A router has routes to several subnets of a classful network in its routing table. A default route is defined on the router but the ip classless command is disabled. If the router receives packets for a subnet that is not in its routing table but is in the same classful network as the other subnets, what will happen to the packets? 13 15 Which statements describe load balancing when RIP is configured as the routing protocol? (Choose two.) 16 • RouterB(config)# router rip • RouterB(config)# router rip 18 When a routing table update is received by a router in a distance vector network, which of the following occurs? 20 When does RIP send routing table updates? (Choose two.) 21 Which of the following can exist in a distance vector network that has not converged? (Choose three.) 22 What happens to a static route entry in a routing table when the outgoing interface is not available? 'study > ccna' 카테고리의 다른 글
[Schizo!, 2008. 10. 23. 23:44, 자료]
   '자료' 카테고리의 다른 글
[Schizo!, 2008. 10. 11. 13:15, study/ccna]
1 Which command or set of commands will stop the RIP routing process? 3 Which of the following functions are performed by a router as routing information travels through the network? (Choose two.) 4 What do distance vector algorithms require each router in the network to send? 6 7 Which command will display RIP activity as it occurs on a router? 9 10 How would an administrator configure a static route for use if a primary route failed? 11 Which statements describe RIP? (Choose three.) 12 A router has routes to several subnets of a classful network in its routing table. A default route is defined on the router but the ip classless command is disabled. If the router receives packets for a subnet that is not in its routing table but is in the same classful network as the other subnets, what will happen to the packets? 13 15 Which statements describe load balancing when RIP is configured as the routing protocol? (Choose two.) 16 • RouterB(config)# router rip • RouterB(config)# router rip 18 When a routing table update is received by a router in a distance vector network, which of the following occurs? 20 When does RIP send routing table updates? (Choose two.) 21 Which of the following can exist in a distance vector network that has not converged? (Choose three.) 22 What happens to a static route entry in a routing table when the outgoing interface is not available? 'study > ccna' 카테고리의 다른 글
[Schizo!, 2008. 10. 11. 13:13, study/ccna]
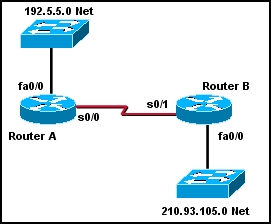
1 What can be concluded about the routing process on a router if the commands router rip and network 192.5.5.0 have been issued? (Choose three.) 2 Which two protocols use an addressing scheme to direct user traffic? (Choose two.) 6 What is the purpose of a routing protocol? 8 How does a router learn about routes to a network? (Choose three.) 9 Which type of address does a router use to make routing decisions? 11 Select the statements that describe link-state routing processes? (Choose three.) 12 Why is it necessary to specify a list of networks when configuring an interior routing protocol? 13 15 Which category of routing algorithms discovers and maintains a topological map of the entire internetwork? 17 Which of the following statements are true regarding the command ip route 172.16.1.0 255.255.255.0 172.16.2.1? (Choose three.) 18 20 Given the command, RouterC(config)# ip route 197.5.2.0 255.255.255.0 192.10.1.1, what does the address 192.10.1.1 represent? 21 Which of the following conditions must be met in order for a network to have converged? 'study > ccna' 카테고리의 다른 글
[Schizo!, 2008. 9. 19. 10:51, 취미생활/music]
'취미생활 > music' 카테고리의 다른 글
[Schizo!, 2008. 9. 15. 05:04, 취미생활/movie]
청주 날씨는 어때요? 예 좋아요~ㅋㅋ '취미생활 > movie' 카테고리의 다른 글
[Schizo!, 2008. 8. 27. 00:12, 정보]
자주 애용하던 외국의 웹하드(http://www.esnips.com/) 사이트가 몇 달 전부터
접속이 안되더니 오늘은 방송통신심의위원회에서 지정한 불법정보사이트라고 뜬다. 하지만 들어갈수 있는 방법이 있다. http://www.stuffunblocker.com/ 이사이트를 거치면 접속이 가능하다. '정보' 카테고리의 다른 글
[Schizo!, 2008. 8. 16. 11:43, 취미생활/game]
아마 많은 분들이 리얼텍 HD오디오를 사용하실듯 하네요
1.0때는 EAX On으로 해결 가능했던 이문제가 1.1패치후 EAX OPENAL호환모드가 불가능 해짐에 따라 사운드가 나지 않는 당황스런 상황이 발생... 하루 종일 삽질후에 2K 쪽의 테크 포럼에서 답변을 찾았네요 솔루션은, 1. Realtek의 최신 드라이버를 설치합니다 (www.parkoz.co.kr의 파워 다운로드를 이용하셔도..) 2. 다이렉트엑스 최신 버전을 설치합니다 (이건 뭐 필요 없음..) 가장 중요!!!! 3. 제어판 - 소리 - 녹음탭 - 오른쪽클릭 - 사용할수없는장치표시 체크- 스테레오믹스 오른쪽클릭 - 사용함체크 한마디로 스테레오 믹스 문제였습니다 -_- 모쪼록 많은 분들이 해결 하셨음 하는 바램입니다.. 아무튼 즐거운 바이오 쇼크!!! P.S 아 덤으로 오토패치 안되는 현상 땜시 고생하시는 분들, 그거는 계정땜에 그러니까 다른 계정에서 설치하시고 모든 사용자가 플레이할수 있음 체크하심 됩니다... ^^ '취미생활 > game' 카테고리의 다른 글
[Schizo!, 2008. 8. 12. 15:29, 취미생활/game]
1.게임에 들어가서 치트를 칠 마을에 들어간다. 2.먼저 [Ctrl+x]를 친다. 3.창이 뜨면 이 중에서 골라서 치고, 엔터를 누른다. stopwatch - 24시간 잠시멈춤/재개하기
'취미생활 > game' 카테고리의 다른 글
[Schizo!, 2008. 8. 12. 13:15, 취미생활/game]
http://www.emulcrash.com/game_list_bbs/view.php?code=support_list_ps2&post_num=1208393247&no=180&search_list=&search_contents= '취미생활 > game' 카테고리의 다른 글
[Schizo!, 2008. 8. 5. 17:08, 잡담]
알바 끝나고 휴가 다녀왔다.
동사무소가 시내가 아니라 시외로 배치되서 시내배치자와 다르게 노동을 좀 했다능!! 땀이 많은 체질이라 조금 힘들긴 했다. 동사무소 안에 들어와도, 요즘 고유가시대라 청주시장님이 실내온도 28도 유지를 하라고 지시가 있었다나. 동사무소안은 29~30도--;; 더운게 힘들다... 동사무소알바는 겨울에는 편할 것이다.........ㅋㅋ 추워서 밖에서 일도 안하고 따뜻한 실내에서만 일한다 하더라 ㄲㄲ 사무장님이 해주신 말씀은 잘 새겨야지;후후.. '잡담' 카테고리의 다른 글
[Schizo!, 2008. 8. 1. 11:29, 잡담]
동사무소 알바 마지막날. '잡담' 카테고리의 다른 글
[Schizo!, 2008. 7. 4. 00:03, 취미생활/game]
'취미생활 > game' 카테고리의 다른 글
[Schizo!, 2008. 6. 24. 21:35, 잡담]
신의 알바라는 시청 알바에 당첨되었다~! 청주시(시장 남상우)는 대학생 아르바이트 신청자를 대상으로 방학기간 중 시청 산하에서 근무할 대학생을 선발했다. 시는 각동 주민센터를 통해 지난 6월 9일부터 18일까지 접수한 결과, 아르바이트를 신청한 인원은 총 1,509명으로 선발대상 215명에 대해 기초생활수급자, 차상위계층, 차상위의료특례자, 부모중 1인이 장애(1~4급)인 세대의 자녀 142명을 우선하여 선발하고 나머지 신청자 1,367명중 73명을 6월 24일 오후2시에 청주시민회관에서 공개 추첨을 실시하여 18대1의 치열한 경쟁률을 보였다. 이렇게 관공서 아르바이트가 높은 경쟁률을 보이는 이유는 하루 31,000원 총 24일간 74만4천원의 임금 수준이 만족스럽고 또한 비교적 안정적인 근로조건 등 대학생들이 선호하기 때문인 것으로 분석됐다. 한편 대학생 아르바이트에 선발된 학생은 청주시 산하 부서에 배치되어 7월 7일부터 8월 1일까지 근무하게 된다. 시 관계자는 “이번 아르바이트 기간중 학생들이 좋은 행정 경험을 하고 돌아가도록 만전을 기할 계획”이라고 밝혔다. '잡담' 카테고리의 다른 글
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
GTA4 하마치 3.0 해킹 티스토리 초대장/ 티스토리초대 스타크래프트2 율량 데몬 최신버전 비보이 zn40 UK B-Boy Championships CCNA 2 - Module 11 Exam 크레이브 GTA4 치트 정보처리산업기사 GTA4 치트키 김사랑 진중권 블로그 100분토론 디워 티스토리초대 마재윤 모토로라zn40 티스토리 초대장
BLOG Total Visitors
Today Hit, Yesterday Hit 
|
||||||||||||||||||||||||||||||||||||||||||||







 commandline.alz
commandline.alz
 invalid-file
invalid-file
 invalid-file
invalid-file